Implementation of Zero Trust Environment through Cloud Security Controls
Covid pandemic has made the traditional perimeter-based network defence obsolete. Customers expect organizations to maintain security controls similar to controlled/organizational environment in work from home scenario too and getting accustomed to “Zero Trust” environment would be a perfect solution to address all statutory, compliance and regulatory security requirements.
Cloud applications and the mobile workforce have redefined the security perimeter. End users are bringing their own devices and working remotely. Information is being accessed outside the corporate network and shared with external collaborators such as clients, partners and third party vendors. Corporate applications and data are moving from on-premises to hybrid and cloud environments.
The new perimeter isn’t defined by the physical location(s) of the organization—it now extends to every access point that hosts, stores, or accesses corporate resources and services. Interactions with corporate resources and services now often bypass on-premises perimeter-based security models that rely on network firewalls and VPNs. Organizations which rely solely on on-premises firewalls and VPNs lack the visibility, solution integration and agility to deliver timely, end-to-end security coverage.
Today, organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, applications, and data wherever they are located. This is the core of Zero Trust.
What is Zero trust
A zero trust “ZT” environment is an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data breaches and limit internal lateral movement. ZT is not a single architecture but a set of guiding principles for workflow, system design and operations that can be used to improve the security posture of any classification or sensitivity level information.
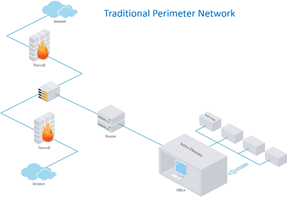
Traditional perimeter security controls
A traditional security architecture would consist of Firewall/UTM, Network Intrusion detection and prevention system, Centralized Anti-Virus, Anti-Spam, Perimeter and host based data loss prevention, Domain controller (Active Directory), SIEM, Patch management tools etc…
Approach required to ZT implementation over cloud
One should consider technology and product agnostic approach to leverage ZT architecture and protect organizational assets and investments. A four step approach is recommended for ZT implementation using cloud controls. Assess, Audit, Apply and Assure (A4) is mentioned below:
Assess
Comprehensive security assessment has to be performed to identify vulnerabilities related to endpoints, servers, web, mobile and other environments.
Audit
During this phase one has to define the security architecture, and deliver a detailed strategic plan as per their compliance, regulatory and statutory requirement.
Apply
Detailed plans and Architecture designs are to be developed that include all technology and system components necessary to deliver the final solution.
Assure
Continuous monitoring identity management, access logs of end points, applications, workloads and network has to be performed at this stage.
Cloud solutions that can meet ZT requirements
Even though we consider solutions that are provided by Microsoft Azure, similar kind of solutions are available on all cloud service providers.
Authentication
Implement Multifactor authentication: MFA, 2FA, or third-factor authentication, are essential in achieving Zero Trust. Microsoft Azure AD provides support to MFA and Single Sign On (SSO) functions.
Access control
On a perimeter based network access restrictions are enforced through group policies of traditional active directory. The same can be achieved using cloud based mobile device management (MDM) solutions like Microsoft Intune.
Conditional Access
Azure Active directory provides conditional access restriction functions like User/Group based, IP based, device based or application based. It also provides Real-time and calculated risk detection.
Micro segmentation (Application and Network Firewalls)
Micro-perimeters act as border control within the system, identity/credential, and preventing any unauthorized lateral movement. The organization can segment based on user group, location or logically grouped applications. Micro segmentation can be achieved using Azure’s ASG and NSG services.
Monitoring
Azure’s Security Center (Azure defender) helps us to figure out where the anomalous activity is occurring and monitor all the surrounding activity. Inspect, analyse and log all traffic and data without interruption.
Policy enforcement
Different organizations require types of compliance requirements. Organizations can easily implement/enforce security policies and controls using the security benchmarks, blueprints and policies functions of Azure.
Key Management
One can use Azure Key Vault is Microsoft’s cloud service for securely storing and accessing secrets including passwords, SSH/API keys.
End point protection
Mobile device management solutions like Intune can be used to control how devices are used, including mobile phones, tablets, and laptops. You can also configure specific policies to control applications.
Security Operation Center
Cloud based SIEM solutions like Sentinel can be utilized to help security teams collect and analyse large amounts of data at scale to catch emerging network threats.
Conclusion
Zero Trust security model is most effective when integrated across the entire digital environment, most organizations will need to take a phased approach that targets specific areas for change based on their Zero Trust maturity, available resources, and priorities. It will be important to consider each investment carefully and align them with current business needs.